How To: Drop Everything! Here's How to Secure Your Data After Heartbleed: The Worst Web Security Flaw Ever
This time it's serious. Really.The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.This bug is so bad, it not only breaks encryption, but causes affected servers to spit out all kinds of personal information, from user passwords, to credit card numbers and e-mail addresses, and even the private keys that make HTTPS encryption work in the first place.Even worse, Heartbleed leaks all of this information without leaving any trace whatsoever. If you used the Internet at all, especially during the past week, chances are this bug has affected you in one way or another.
What Exactly Is OpenSSL Anyway?OpenSSL is an open-source SSL (secure socket layer) encryption library used by hundreds of thousands of secure websites. Everything from banks and email, to Amazon and Google rely on it to keep your connections encrypted.You probably know it by the small lock symbol in your address bar, or the "https" (compared to just "http") you see at the beginning of a website's URL. It is used by almost two-thirds of the internet to secure the transmission of personal information from web applications, emails, instant messaging, online shopping, and even some VPNs.The Heartbleed bug gives cyber criminals, hackers, and since Monday, curious bystanders a wide-open door to much of the private information we all thought was secured by SSL.
So, How the Heck Does All of This Work?When your computer is setting up a secure connection with a website, some applications send a signal (or a "heartbeat") to the site's server through SSL. The heartbeat works by sending information to the server, which the server then sends right back in order to show that the connection is secure and working properly.Applications can send a heartbeat using whatever arbitrary message they want, of whatever length they want (up to 64 kilobytes), and then check to make sure the response from the server is equal to what they sent.For example, if the heartbeat consisted of the word BASED, which is five characters long, the application would tell the server "here's a five-character long heartbeat. It's value is BASED." The server would then receive the heartbeat request, and return the word BASED as a five-character long response.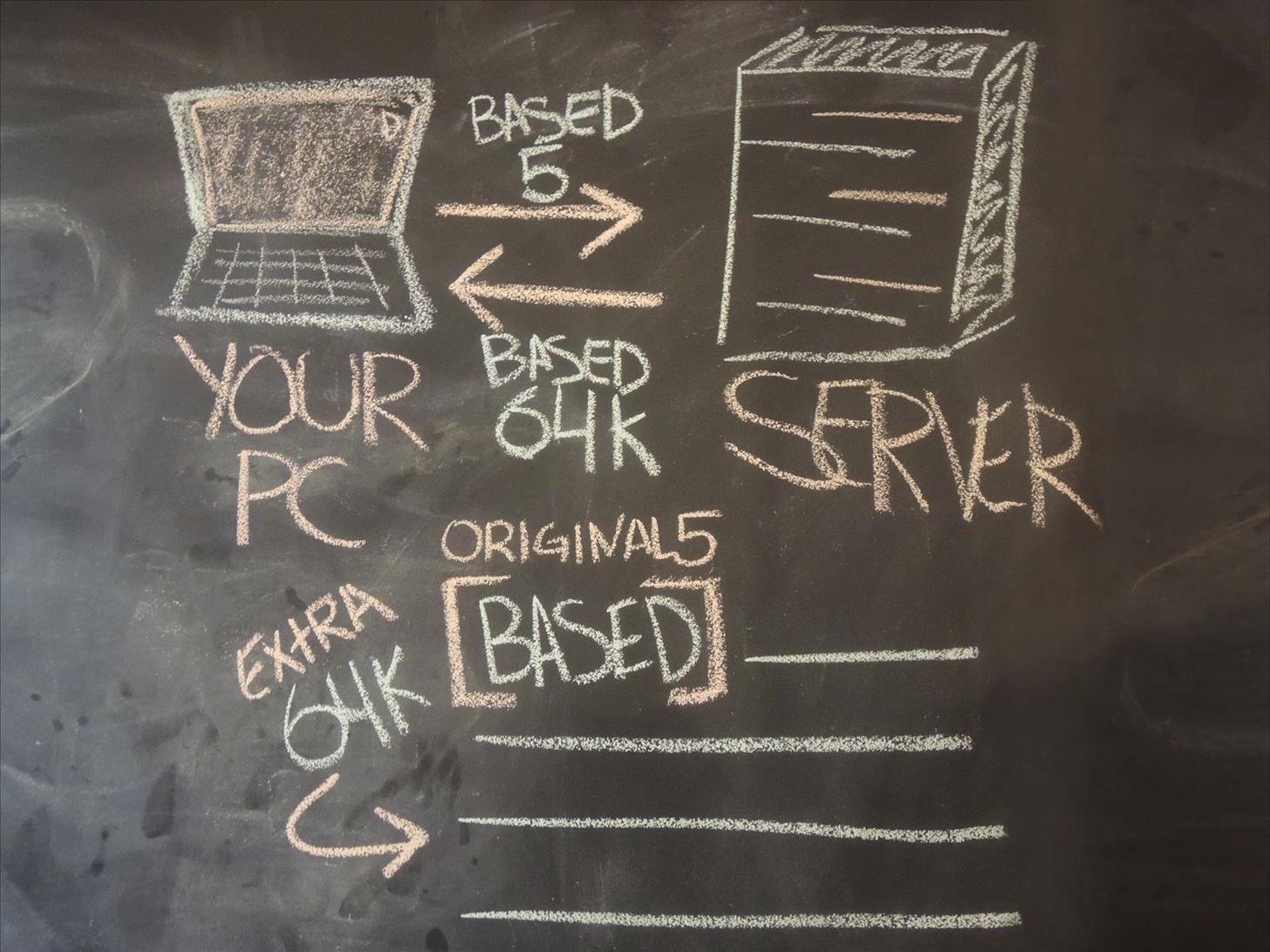
So What's the Problem?Due to the flaw in OpenSSL's implementation of this heartbeat, a giant leak was opened up. In short, the server wouldn't verify that the message sent was the length the application said it was, resulting in the server responding to malicious applications with an arbitrary amount of data that was left over in server memory. That memory could (and often does) contain sensitive information.So, let's say the heartbeat being sent from your computer consists of the word BASED again, but this time the application tells the server that the information being sent is 64,000 characters long. Obviously this is not true, as the word BASED only contains five characters.Once the server receives this information, instead of checking to make sure the message sent matches the stated length, it simply sends back the word BASED along with a total of 64,000 characters of whatever happens to be in memory after that point, in order to satisfy the request for a 64K heartbeat. As for the supplementary information contained in those 64,000 characters? Well, it can include private information, such as usernames and passwords for email, banking, and social media accounts. Worse yet, the private keys that keep SSL safe in the first place.All the hacker needs to do is create a script, which could then do all the dirty work and grab information. In fact, many such scripts are now floating around the internet and are so simple to use, that your computer-savvy little brother could be using it. Worst of all, you wouldn't even know they did it, as this exploit leaves no traces behind.XKCD's latest posts sum it up quite well. Image via xkcd.com xkcd on Heartbleed Image via xkcd.com xlcd Explains Heartbleed
Which Sites Were Affected?While the majority of websites across the internet that offer encryption and run on Linux were susceptible to this flaw, some were late to the party to fix the issue, which has since been remedied with an update to OpenSSL.Out of all the victims, Yahoo got hit harder than most other sites because they were so late to patch the Yahoo Mail servers, exposing many of their user's passwords for more than 24 hours.While some major sites and services like Google, Akamai, CloudFlare, and Facebook were warned ahead of the public disclosure, most have been scrambling to patch their servers as quickly as they can.Other popular sites that were affected by the Heartbleed bug included Instagram, Pinterest, Tumblr, Intuit, Dropbox, Minecraft, Imgur, Flickr, RedTube, OkCupid, and XDA, but all have been patched now. However, this does not mean that all sites on the web have been fixed, or that your data wasn't compromised before they were.This bug was introduced into the OpenSSL source code over 2 years ago. Because exploiting it can be done without leaving a trace, it's safest to assume that all our passwords have been compromised.The programmer who introduced this bug has denied conspiracies that this flaw was intentional, but even so, it's very possible that the NSA's cryptographers (as well as those of other governments) had silently discovered this bug earlier on and have been using it to intercept sensitive communications.
How to Protect YourselfIf you've used your computer since Monday to log in to banking sites or check your email, there's a very high chance that your passwords have been stolen, even though most banks state they weren't susceptible to this bug. If you've logged into any secured site in the past two years, it's safest to assume the same. Please enable JavaScript to watch this video.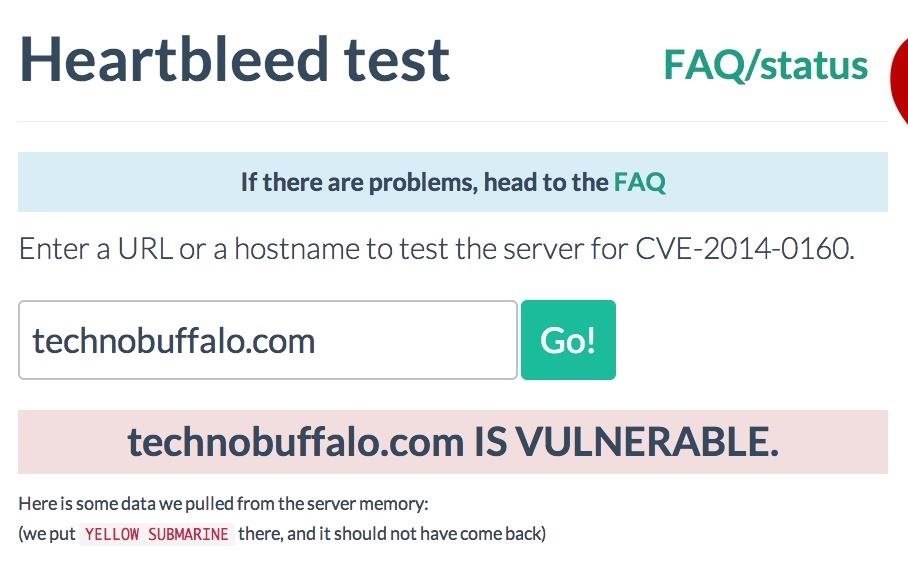
Step 1: Don't Visit Websites That Are STILL VulnerableYes, there are still sites out there that are vulnerable, either because they don't know about the bug yet, or haven't been able to patch it just yet. To check if a website is currently susceptible to the Heartbleed security flaw, head over to the Heartbleed checker and type in the full domain name of the site in question. If you see anything other than the red note stating the site is vulnerable, then it's safe. Either the site has already been patched, or was never susceptible in the first place. And just for the record, WonderHowTo was not affected, so don't worry.If you do see the red vulnerable message, DO NOT VISIT THAT WEBSITE AND DO NOT TRY TO CHANGE YOUR PASSWORD YET. Doing so would only increase your chances of having your information stolen.
Step 2: Change All of Your PasswordsThis is not a drill. Once you've verified that a site is not vulnerable using the link above, visit it and change all of your passwords. This is especially important for Yahoo users as knowledge of their vulnerability became widespread on Monday and Tuesday. Here are a few tips to use when creating your new passwords:Use passwords that consist of eight characters or more that contain special characters, like any of the ones that live on the number row of your keyboard. Do NOT to use the same username/email and password combination for multiple sites. If someone hacks into one of your accounts, they'll be able to hack into ALL OF YOUR ACCOUNTS. Which brings us to our most important step...
Step 3: Use a Password ManagerFace it. You can't remember all of these passwords. Nobody can. It's time to get your self set up with a secure password manager application that will lock everything down for you. The good news is there are some very trustworthy options available. We like LastPass and Dashlane the best. Both consist of web browser plugins that replace your browser's very insecure password manager, encrypting them with a master password that is never stored anywhere.That's right... Your master password never leaves your computer. It's used to generate a strong private key that encrypts and decrypts all your data locally, before ever sending anything online. Even if someone were to hack your computer—and the LastPass or Dashlane servers—they still wouldn't be able to get your passwords without your master password (which is never sent over the internet).We found Dashlane to be the easiest to set up and use as it grabs all your currently saved passwords automatically, but its pro version (which securely syncs encrypted versions of your passwords across Macs, PCs, Androids, iPhones, and iPads) is a little more expensive than LastPass.LastPass is powerful, but does occasionally get confused about what your current password is when you go to change your passwords. Again, they offer a free version, but you have to pay for the pro version to sync with your mobile phone. Still, at $12/year, there's really no excuse. Frankly, I'd be far less inclined to trust them if they didn't charge for the service.
How to Use DashlaneThe good news is, it's so easy, you won't need a tutorial. Just head over to their website and install the software. It'll walk you through everything, automatically pulling in and encrypting any saved passwords from all your web browsers.The biggest reason why I prefer Dashlane is if you forget your master password—tough luck. That is the only key to your data. There is no way to override it.That said, the premium version that syncs across your various computers, tablets, and phones is a little more expensive at $30/year, so LastPass's free version is going to be your best bet if you're allergic to spending money.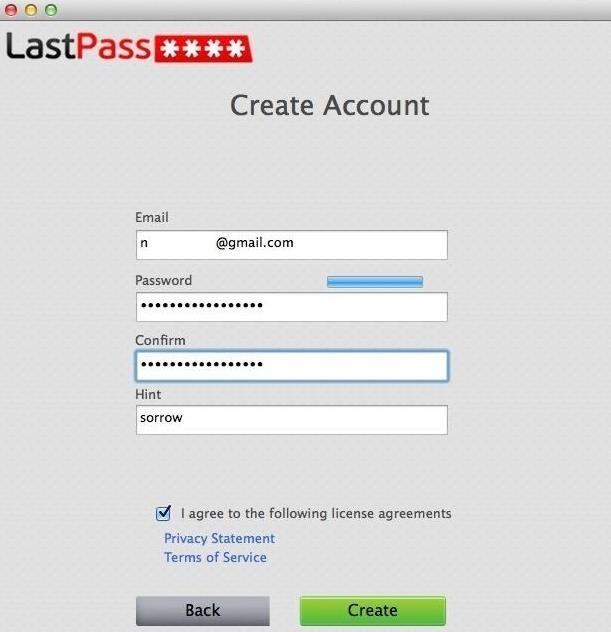
How to Use LastPassDownloading LastPass on your Windows or Mac is pretty easy. Just head over to the LastPass website and download the version specific to your PC.Once it's downloaded, you'll be asked to create an account for LastPass. All you need is an email and a good password. Once that's done, make sure to have all of your web browsers closed because installing LastPass will automatically close & re-open them. Install and proceed when ready. There will be slightly different ways of setting up the program depending on the browser you use. Below, you can see LastPass being installed on Chrome as an extension, which is simple enough to do. The Chrome extension will then create a LastPass icon at the far right of the address bar. Tap on it and log in with the credentials you entered earlier in the installation stage. Now feel free to log in to any one of your banking, email, or social media accounts. In the login boxes, you'll see two small asterisks indicating that LastPass is at work, ready to securely encrypt your passwords using your master password. Your web browser will ask if you want LastPass to remember this password and username combination for the future. If you select yes, it will redirect you to the LastPass settings. All of the information will be filled out automatically, so just click "Save" at the bottom when you're ready. You can also change the password for this specific account here. If you tap on the LastPass icon in the address bar, you can check out the following:LastPass vault Sites that you've secured through LastPass Forms (info, credit cards) that you've filled out and saved Generate a random password Encrypted notes It took me about five minutes to set everything up, and I suggest you do the same.
What if You Lose Your Master Password?If you forgot your master password for your LastPass account, not to worry. You can simply get an email sent with a temporary password to log in, where you can then enter a new one. This peace of mind may be helpful to some, but the fact that this data is recoverable without a master password leaves me a little uneasy.
Step 4: Clear Your Browser's Stored PasswordsOnce you've safely locked down all your passwords in your new password manager, it's very important that you don't forget to clear the passwords your browser has saved. Many people don't realize this, but today's modern web browsers (with the surprising exception of Internet Explorer on Windows 8) still save unencrypted copies of all your "remembered" passwords in plain text. Here's how to clear them (and see them).
In FirefoxClick the "Firefox Menu" Click "Options" or "Preferences" Click the "Security" tab Click "Saved Passwords..." Click "Remove All"
In ChromeClick the "Chrome Menu Button" in the upper-right Click "Settings" Click "Show advanced settings..." at the bottom Click "Manage saved passwords" under "Passwords and forms" Highlight all of the websites in the list Press "Delete" on your keyboard.
In Internet ExplorerIf you're on Windows 8 or newer, your Internet Explorer passwords are stored securely, so no need to clear them.Open "Tools" (or the "Gear Menu") and click "Internet Options" Click the "Content" tab Click "Settings" under "AutoComplete" Click "Manage Passwords" Remove each one
In SafariClick on the "Safari" menu Click on "Preferences" Go to the "Passwords" tab Highlight all of the websites in the list Hit the "Remove" button
Step 5: Change Chrome's Default SettingsBy default, Chrome doesn't check for revoked SSL certificates. If that makes no sense to you, don't worry. Just know that checking a box will keep you more secure. Here's our guide on how to fix it.
Stay Safe, Stay SecureThat's it! Going forward, if (or rather when) the next security breach happens, you'll have the peace of mind of knowing that just one password was compromised, and resetting it is as easy as visiting to that one site and having your password manager generate a new secure password for you so that you won't have to worry about remembering.You also won't have to worry about which other sites you've been using the same password on.
Original bleeding heart and passwords code images via Shutterstock
How to Root Motorola's Droid X cell phone from Verizon
I assure you, Siri, it's nothing personal. Mobile Leer en español Get rid of Siri App Suggestions on your iPhone's lock screen. I assure you, Siri, it's nothing personal.
How to Disable Lock Screen Security While in Trusted
Park your car at a safe parking space. Now take out your iPhone and launch the Maps application. It does not matter if you use Google Maps app or the stock Maps as this trick works on both. Now using the device's GPS navigate to the location you are currently standing in - this should be the location of your car as well.
iOS 10 Maps: All the New Features and How to Use Them
I have deep admiration for font designers. Their attention to detail, commitment to their craft, and discipline are truly unique. That's why every time I hear there's a tool that can turn my handwriting into a font I run to try it. There's a certain magic to the act of turning your squiggly letters
Create Your Own Custom Characters or Fonts with Private
Step 1: Making the LED lights dance to your music Objective here is to use the A/D converter on Arduino to read input sound and light up a set LEDs to reflect the level of the sounds volume. The LEDs are controlled from Digital pins 3, 4, 5,6.
Make LED lights dance to music (easy and cheap) - YouTube
We know that the idea sounds great, so don't hesitate to learn how to enable Kids Mode on Samsung Galaxy S5, how to create a profile and setup Kids mode, how to make an emergency call while in Kids Mode on or how act in case of forgetting your PIN. Let's begin! How to Enable Use Kids Mode on your Galaxy S5:
How To: Enable Kids Mode On A Samsung Galaxy Tab 3 7.0
Whether if it's to play games or watch Netflix or YouTube, children love using our smartphones and tablets. As an uncle of many, I don't mind my nieces and nephews using my gear, but I do mind them opening apps they have no business being in, like my photo gallery or messaging app.
Enable Kids Mode on Any Android Phone or Tablet [How-To
It probably knocks off a quarter inch of usable screen display space. The screen is usually a quarter of an inch taller because there are no hardware buttons in the first place. I don't get the impression soft key phones have smaller bezels than phones with hardware buttons.
keyboard - Need table of key codes for android and presenter
Apple Music in iOS 9 gets a much-needed redesign The iOS 9 public beta cleans up Apple Music's numerous options for a more streamlined listening experience.
How To: Find Songs by Lyrics in Apple Music for iOS 12 — With
Navigation app Waze occasionally gives you the option to have a celebrity voice provide directions for your trip, like this famous European with a funny voice, or this decidedly less-famous European with a funny voice. It'll be hard for Waze to top its latest addition to the roster, though. He's the
How To Get Morgan Freeman Voice On Waze GPS Navigation App
In the Logitech Gaming Software window, click the on the lighted, colored part of the mouse. In this example, the LED color is set to red, but it may be a different color on your computer. In the next window, look for the color wheel. The color with the glowing highlight is the selected color.
Amazon.com: color changing wireless mouse
How to do Session Hijacking?? Session Hijacking is also one of the attack that is commonly done on websites.For a brief overview on it, Go on with my article.
Session Hijacking : How to hack online Sessions
Friends vs Acquaintances. That being said (and it felt pretty good to say it), I needed a way to minimize all of the political crap that was showing up in my News Feed. The most drastic solution was to quit Facebook altogether. I seriously considered it but decided against it since Facebook is how I keep in touch with friends that I don't see
How To Remove Friend List? - Facebook
With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad.
FYI: If you are using FT8, please sync your PC clock - reddit
When clearing any form of data from your browser, it's best to close and re-open the browser after the clearing is complete in order to finalize the process. Deleting your browser's cache is not the same thing as deleting cookies.
How to Clear Internet Cache in Every Major Browser
0 comments:
Post a Comment